After recently reviewing my privacy settings for Microsoft, I noticed something that was both alarming and reassuring.
The Reveal
It is always a good idea to review your privacy settings every year or so when dealing with companies on the internet. You never know if they’ve added something new or changed something without telling you.
I was recently doing this on Microsoft’s account page. Like most big tech companies, they don’t make it easy to see everything on one page, so you have to go hunting around lots of different screens to find what you really want.
I eventually came across this page, and it was initially quite alarming:
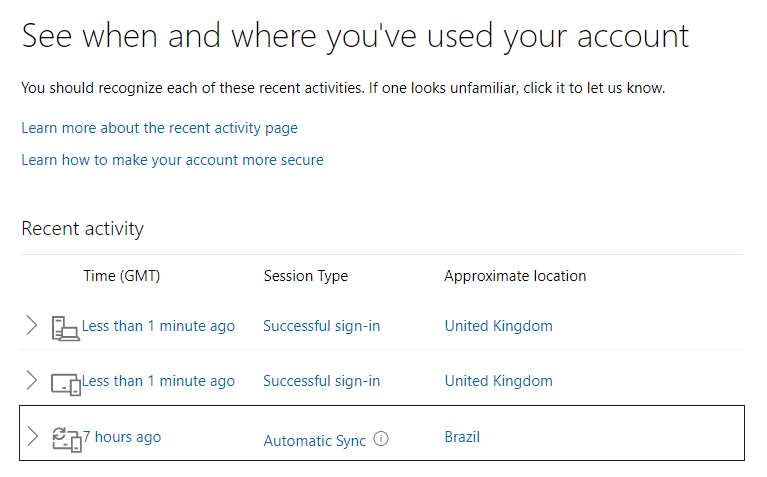
I’ve logged in from where? Brazil? I don’t remember that holiday… When I dug a little deeper:
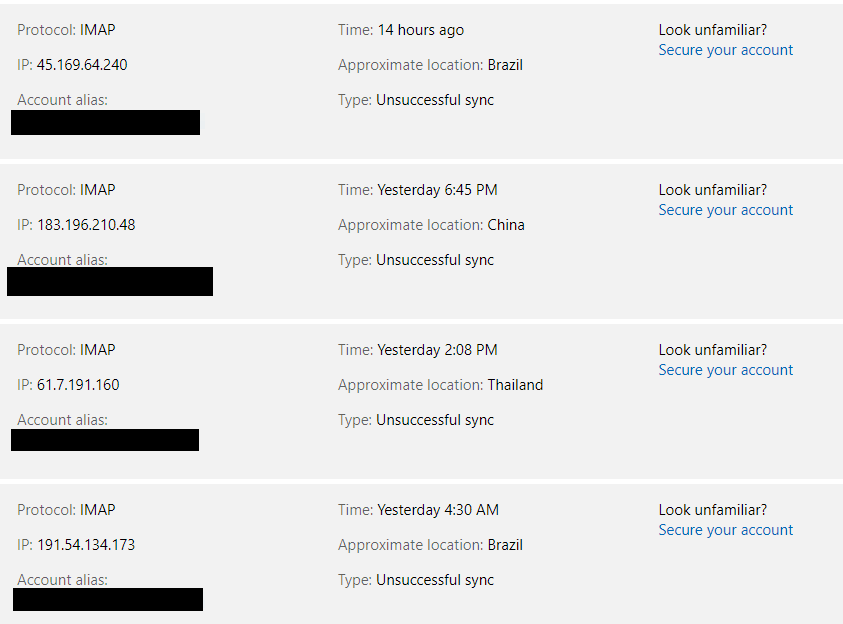
Ooer. In the past few days, login attempts to my account have been made (thankfully all unsuccessfully) from the following locations:
Brazil, China, Egypt, India, Iran, Italy, Malaysia, Mexico, Norway, Russia, Slovenia, Thailand, Vietnam, and Yemen.
What is happening here is likely a hack known as credential stuffing. This is when an attacker tries various combinations of email addresses or username and guessed passwords.
In this case the attacker is using IMAP, meaning they want to gain access not to my whole account, but just to my emails.
How is your login leaked?
Login credentials refers to anything that is used to log into your account. Usually at least a username, an email address and a password.
Your email address is probably already public knowledge. If you use a permutation of your name or username, it’s public. If you’ve ever received a spam email message, it’s public. There is nothing you can do about it now, and that is a fact of life on the web. Once something goes on the internet you can never take it down.
Your password may or may not be public. A password will end up being public knowledge if:
- A service you use does not have sanitary password† storage and gets hacked
- A service you use does not have sanitary password† storage and routinely lets its employees see your password
- It is an easily guessable password like 1234, qwerty, or a common name‡
† Unsanitary password storage can be anything from weak hashing, to a lack of salting, to just storing your password in a plain old text file
‡ This is not an exhaustive list of what is an easy to guess password. A good rule of thumb is if it did not take you some effort to remember it, then it’s probably easily guessable.
In some cases, if your password is leaked together alongside your email address, that will tell an attacker everything they need to know to login to, and successfully hack, your account.
Thankfully, as companies become more aware of secure password storage, the likelihood of credentials being leaked starts to decrease. But please don’t be lulled into false sense of security. Such hacks of companies you have entrusted your data to still happen far more often than they should.
What does an attacker to with public credentials?
I should state here that credential stuffing is very rarely a targeted attack – in other words it is indiscriminate. The hackers are not out to get you at a personal level. They’re out to get anyone they can. For most people, threat actors only exist to take advantage of weak security. It’s cheap and so offers good returns. The vast majority of people will never be direct victims of targeted hacking by hacker collectives, industrial spies, or foreign nations.*
*And yet people routinely hand over data and control of their lives to Silicon Valley startups all the time, which totally baffles me. Makes you wonder who the real threat is.
If hackers know an email address and they know a password, attackers will “stuff” these passwords into login forms. There is no real intent there, it’s just to see if the login is a success. They might get lucky, they might not, but it is cheap to try.
That’s why you can see so many examples of failed login attempts. But as long as the attempts did not succeed, everything is golden.
Why only go after IMAP?
In the example above, all of the failed attempts have been made on “IMAP”.
IMAP is a protocol used for email. Like HTTP is used for HTML pages, IMAP serves you emails. If an attacker ever did get access, they wouldn’t be able to edit the account information, but they would see the email. But if it doesn’t give full access, then why go after IMAP in the first place?
Well, every email service has the same IMAP interface, so it is far easier to automate stuffing attempts across many services.
Also, I don’t get a 2FA login notification every time I log in to IMAP. Software like the email app on my phone would constantly trigger these notifications, which would make the security unusable. So, it isn’t turned on. This makes it much more likely that an attacker would be able to get in if they had the right credentials. And once they do, they would be able to see any login warning emails and erase them before they get synced to my inboxes.
IMAP would also let an attacker scrape all my contacts. They could then use this info to send spam to my contacts. They could send phishing emails pretending to be me or someone I know, to trick people into clicking on links or downloading bad attachments.
Thanks to my 2FA it would take additional effort to gain access to my account controls to fully take over, but I doubt that is the real aim. It is far more profitable for an attacker to just silently use an email account, hoping they never get noticed. For example: to take over other accounts.
Having email access would allow taking over any social media accounts that used that email address for account recovery. The attacker clicks “reset password”, enters the email address they now can access, and then they use the link in the recovery email sent. Now the attacker now has full control of a social media account. If it has lots of followers, it is now a lucrative hub to use to spread all manner of nasty content.
Protection
If you want to take extra measures to protect yourself here is some advice:
Passwords
Unique passwords across your logins. A different password for every login you own means if one gets leaked, it can’t be used on any of your other accounts. It also means that after a hack you must only spend effort changing a single password.
Unique passwords different from every other password ever used by anyone is helpful. If someone else happened to have the same password as you, an attacker could try different combinations of email adresses and entries from a dictionary of leaked passwords. Credential stuffing won’t work if your password hasn’t been seen in public before.
Use a password manager to make it easier to remember long, unique, random passwords. I use software called KeePass, but even a plain old physical notebook is better for most people than using poor quality passwords.
Extra Security Options
2-Factor authentication is a must for important accounts that serve as your single point of failure. Non-SMS** based 2FA requires you to have a physical token or device to log in as well as your password. Pick any 2 from something you have, something you are, and something you know.
In case a hacker does make it past the login and wants to gain access to your account controls, 2FA would require an attacker to steal a physical device from you, like a phone. This means attackers from halfway around the world are out of luck.
**SMS based 2FA is not recommended as it can be bypassed if your mobile phone company doesn’t practice good security.
If social media sites let you, turn off the email address shown next to the “recover password” link. A good secure service should always ask you to enter it manually rather than filling it out for you. That increases the work an attacker must do to guess which email address belongs to you.
What now?
I praise Microsoft for being transparent enough to present this information. Although initially alarming, it is nice to know that my security has prevented these logins from succeeding.
I also know (from times I’ve been on holiday abroad) that if any attempts do get past the initial password stage, my 2FA blocks them and I also get a notification about a login from a new location, and it is always reassuring to use this as a test for security. Security that isn’t tested is theatre at best.
Microsoft also sends a notification about new logins to my backup email address, just in case an attacker deletes the original from my main inbox.
If you own a Microsoft account and want to review these settings, you can do so at this link: https://account.live.com/Activity. If you don’t trust the hyperlink (fair enough) you can get to it from clicking on your profile icon in a logged in Microsoft page > Account Settings > Security > Review my activity. While you’re there, have a flick through the rest of the settings, particularly the privacy settings, which might reveal a lot more than you would hope.
If anyone else knows of services that offer similar notifications or details hidden away, leave a comment so others can find it. Some digging around shows GitHub offers similar information.
I’ve treated credential stuffing as a very surface level here, if you want a more in depth write-up, OWASP have produced a very nice document published on GitHub as additional reading.
You made it to the end, hurrah! As a well-done reward for reading, here’s a relaxing picture of a field to aid in your mindfulness:

click through for full size

KeePass is unfortunately not anymore maintained for macOS, since the code is open source some devs took it under their wings to make nice password managers and most of them are not free though and I understand, every needs to eat.
As an alternative Vivaldi’s password manager (sorry I’m biased of course) is a good one as passwords are encrypted and synchronized across your devices. 🙂
I tend to have duplicates in both KeePass and vivaldi. But I need keepass as it can do extra stuff like store notes encrypted, and it works for apps outside the browser.
Thanks for a really interesting article!
Thanks.
What a fantastic, thorough – and above-all, clear and understandable article! I really enjoyed reading about it.
I must admit, I’ve been rather lax regarding 2FA as it’s such an inconvenience for someone like me, who never stays signed-in to anything and always clears cache/cookies. An additional complication for me would be finding some sort of non-SMS way of getting 2FA, as I don’t use a smartphone. I believe some 2FA apps allow you to pre-generate a list of, say, a dozen one-time codes that you can keep on a piece of paper for emergency use, so that might be an option – or of course one of the hardware keys you mention.
As a slight related story, I have a GMail account, which I’ve had since around 2003/4 when GMail was an invite-only experiment. I only use it as a repository for spam these days, nothing serious or important… or so I thought! Last week I almost completely lost access to it, because it didn’t have an up-to-date phone number for me. I entered the correct password, I entered the security-code sent to my alternative e-mail address (a form of 2FA!!!), and I also answered my security question, yet Google in their wisdom decided that this wasn’t sufficient information to prove I was the owner of the account! Seeing as there was literally no other way to authenticate myself, I suddenly realised just how many services I’d used that GMail account to sign-up for, and resigned myself to losing-access to all of those too. Fortunately, I had left Thunderbird open on my desktop PC, and so I drove home and attempted to sign-in from there. Thankfully, Google recognised my sign-in attempt was coming from a web browser with the same IP address as an already-authenticated IMAP session, and let me in.
The moral of the story? Threefold: Firstly, 2FA is great, but if you lose access to your authenticator, you’re screwed, so have a backup-plan if possible! Secondly, protect your email address above all else, as it’s the master-key to all of your other accounts. Thirdly, do an audit of exactly what you’ve used an address for, you’ll be surprised! I have dozens and dozens of accounts I’d forgotten about, scattered across the web! Each one is a potential security risk, so kill any dormant ones.
By the way, fellow Keepass user here. I didn’t realise MacOS support was gone. I just use it because it’s free/libre open-source software, and there are Windows, Linux, and Android versions… and even a J2ME version that runs on old “feature phones”. What irritated me so much about Google not accepting my recovery email address as “proof” that I was the owner of my account, was that being a Keepass user, I have extremely-long, random, unique passwords on every web site, therefore I could only have been me! Additionally, what’s the point of a “recovery address” if you can’t use it to recover your account?
One of the good things about a password manager is you can quickly see which email addresses are used for which services, in case you need to do that audit!
One of my fellows Vivaldi discord chatters made a web app you can use to store 2FA codes in an offline way: https://www.cqoicebordel.net/authenticator/
This isn’t as portable, as you would need to store it only on one machine, but it could be useful if you are absolutely certain you won’t lose access to the device (and keeping your backup codes somewhere safe).
I found similar attacks earlier this year when I reviewed that info and reported them as not me (was seeing Russia, Ukraine and China). Many companies the 2FA SMS code they send is 6 characters and is numbers and letters. 2FA phone app is weak as I have seen many people locked out of their own account because the device with the 2FA app has a fried power port or bad battery or something else.
Apple iCloud will list what devices are logged in.
https://support.apple.com/en-gb/guide/icloud/mm25565a6496/icloud
Google has a similar option I think about what devices are logged in to your account. https://support.google.com/accounts/answer/3067630?hl=en
A 2FA app can lock you out of your account if you lose the recovery codes, but I see that as a strength, not as a weakness.
SMS codes are vulnerable to social engineering attacks performed on mobile phone companies, and they are notoriously bad at falling for these, but app-based 2FA is much stronger as you can’t be hacked remotely.
The app is not locking you out but the device the app it is on does, I have tried to help and explain to people who can’t access their Google account because the phone the 2FA app is on has bricked (one the phone power port caught fire another there battery went bad (you have to have a matching device and a way to charge a battery that can be swapped (it if can).
You should still be able to use 2FA recovery codes – every 2FA system I’ve used has offered 2FA codes. You should be able to use these to log in once, and remove or reset the authenticating device from your online account settings.
They don’t have access to those (Google does not do a great job of explaining things) or the set up might have predated 2FA recovery codes.